Austrian Security Researchers Uncover Multiple Critical Vulnerabilities in VoWiFi – Affecting Austrian Mobile Operator!
Significant global security vulnerabilities and the possibility of eavesdropping in Voice over WiFi (VoWiFi) – one of the prevailing communication protocols in the mobile sector – have been exposed by security researchers from SBA Research, the University of Vienna, and the CISPA Helmholtz Center for Information Security in Saarbrücken. VoWiFi Security: Poor Grades in Practical Tests!
VoWiFi (also known as WiFi Calling, Voice Boost) is already supported by all three major mobile operators and several virtual operators in Austria.
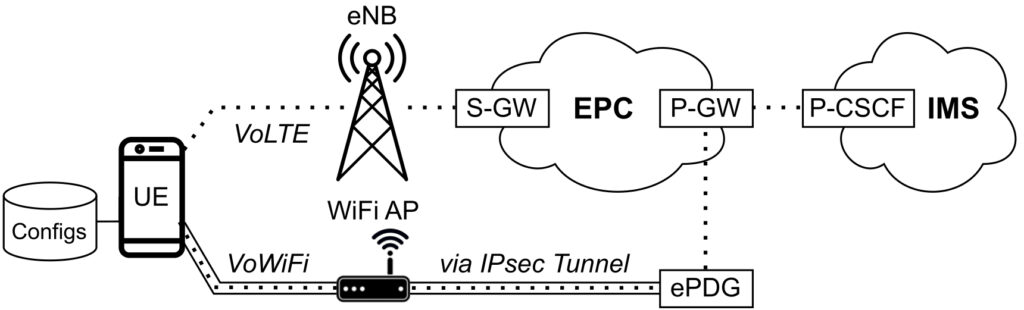
Telephone calls from the telephone (UE) to the exchange (IMS): VoLTE compared to VoWiFi via an untrusted Internet connection.
As part of this research collaboration, the VoWiFi communication channel, mobile operator equipment, and the encryption parameters commonly used in practice were thoroughly evaluated, leading to the discovery of two independent, far-reaching security vulnerabilities. Globally, at least 13 mobile operators (including one from Austria) and most of the virtual operators using their infrastructure have not used random keys for years, endangering the communication security of over 140 million customers. Furthermore, attackers were able to drastically shorten the key length in many new 5G devices with MediaTek chipsets, thereby facilitating attacks. Both vulnerabilities allow attackers to eavesdrop on conversations with little effort.
Vulnerabilities in Core-Routers and Smartphone-Chipsets
During provider-side tests, it was found that some mobile operators used the same private keys for key exchange. Further analysis revealed that the vulnerability was limited to operators using ZTE equipment for their core network. “Overall, more than 140 million customers worldwide were affected by the vulnerability, including in Austria, Brazil, and Russia. Anyone in possession of these (not-so-private) private keys could listen to the communication between the smartphone and the mobile operator without cracking,” says Gabriel Gegenhuber, security researcher at SBA Research and PhD candidate in the Security and Privacy research group at the University of Vienna.
© Niklas Schnaubelt
Access to the keys is available to the affected mobile operators, the manufacturer, and potentially the security authorities of each of these countries. “In the encryption used here, it is crucial that the keys are both secret (i.e., private) and completely random. Neither was the case here,” explains Adrian Dabrowski, PostDoc at CISPA Helmholtz Center for Information Security in Saarbrücken and former Senior Researcher at SBA Research.
© Laura Jahke / CISPA
Additionally, it was discovered that with an active downgrade attack on many new MediaTek chipsets (including 5G), a downgrade to the weakest encryption or Diffie-Hellman group is possible. This is the case even if this group is not supported according to the smartphone configuration. Such a downgrade attack significantly reduces the cryptographic effort required to crack the encryption.
Frequently Outdated Parameters in Use
On the client side, existing configurations on smartphones such as Apple iPhone, Google Pixel, Samsung, and Xiaomi were analyzed, and on the server side, the supported parameters were identified by simulating smartphone connection requests. “We compared these results with the guidelines in the relevant ETSI/3GPP standards and found that up to 80% of the client and server parameters have been considered outdated since 2016 and are therefore no longer intended for use in production systems,” reports Gabriel Gegenhuber, both astonished and concerned. “Thus, there is a significant need for improvement in terms of security for many mobile operators.“
Security Vulnerabilities & Security Research
“Independent research in critical infrastructure is essential for a secure digital society. It identifies such vulnerabilities and subsequently closes them in professional collaboration with manufacturers as part of a responsible disclosure process,” emphasizes Adrian Dabrowski.
© Marcel Lehner
As part of this responsible disclosure process, the Global System for Mobile Communications Association (GSMA) and the relevant providers and companies were informed and given the opportunity to develop updates before the findings were presented to the professional community at the USENIX Security Conference in August. Android updates have been available since May. Updates for ZTE mobile networks have been deployed by most affected mobile operators. In Austria, the ZTE fix was implemented in all affected networks the fastest.
The vulnerabilities found here are not flaws in the protocol itself, but rather implementation errors by the respective manufacturers.
Vulnerabilities:
CVD-2024-0089 – GSMA Mobile Security Research Acknowledgements
CVE-2024-20069 – MediaTek June 2024 Product Security Bulletin
CVE-2024-22064 – ZTE Configuration Error Vulnerability in ZTE ZXUN-ePDG
Read the full Paper Preprint !